Secure file sending With full audit-trail.
Track who accessed your files, when, where, and how many times they tried.
Recipients get one-time credentials. Failed attempts? Everything self-destructs.
The Problem with Email & Traditional File Sharing
No Control or Visibility
Once you hit send, you lose all control. Files live in inboxes forever. You can't track who viewed it, when, or from where. Zero accountability.
Compliance Nightmare
Without audit trails, you can't prove compliance with GDPR, HIPAA, or SOC2. One data breach audit and you're exposed with no evidence of due diligence.
Sound familiar? There's a better way.
How Sealdrop Works
Secure file transfer with complete audit trail in 5 simple steps
Upload & Configure
Sender uploads file (up to 300MB), sets expiration time, view/download limits, and optional password protection. Sender's IP and identity logged via Google OAuth.
Recipient Gets Email
Recipient receives secure link via email. No password yet—just the access URL. Email logged with timestamp in audit trail.
Two-Factor Authentication
Recipient enters their email. System sends second email with 4-digit verification code. Every access attempt logged with IP address. 2-3 failed attempts? Document self-destructs.
Download & Track
Upon successful authentication, recipient downloads file. Every view/download recorded: timestamp, IP address, user email. Full audit trail exportable to CSV.
Auto-Destruction
Document automatically deletes when: expiration time reached, view/download limit hit, or failed login attempts exceeded. Complete audit log preserved for compliance even after destruction.
Sealdrop Solves the Root Problem
Self-destructing documents + complete audit trail
1. Send
Upload your document and configure: who can view it, when it expires, access limits. Everything is logged from the start.
2. Complete Tracking
Every view and download is logged with IP address, exact timestamp, and user email. Complete audit trail you can export.
3. Self-Destructs
The document disappears permanently after reaching view/download limits or upon expiration. Complete audit log of every access.
See It In Action
Complete control and transparency over your sensitive documents
Dashboard Overview
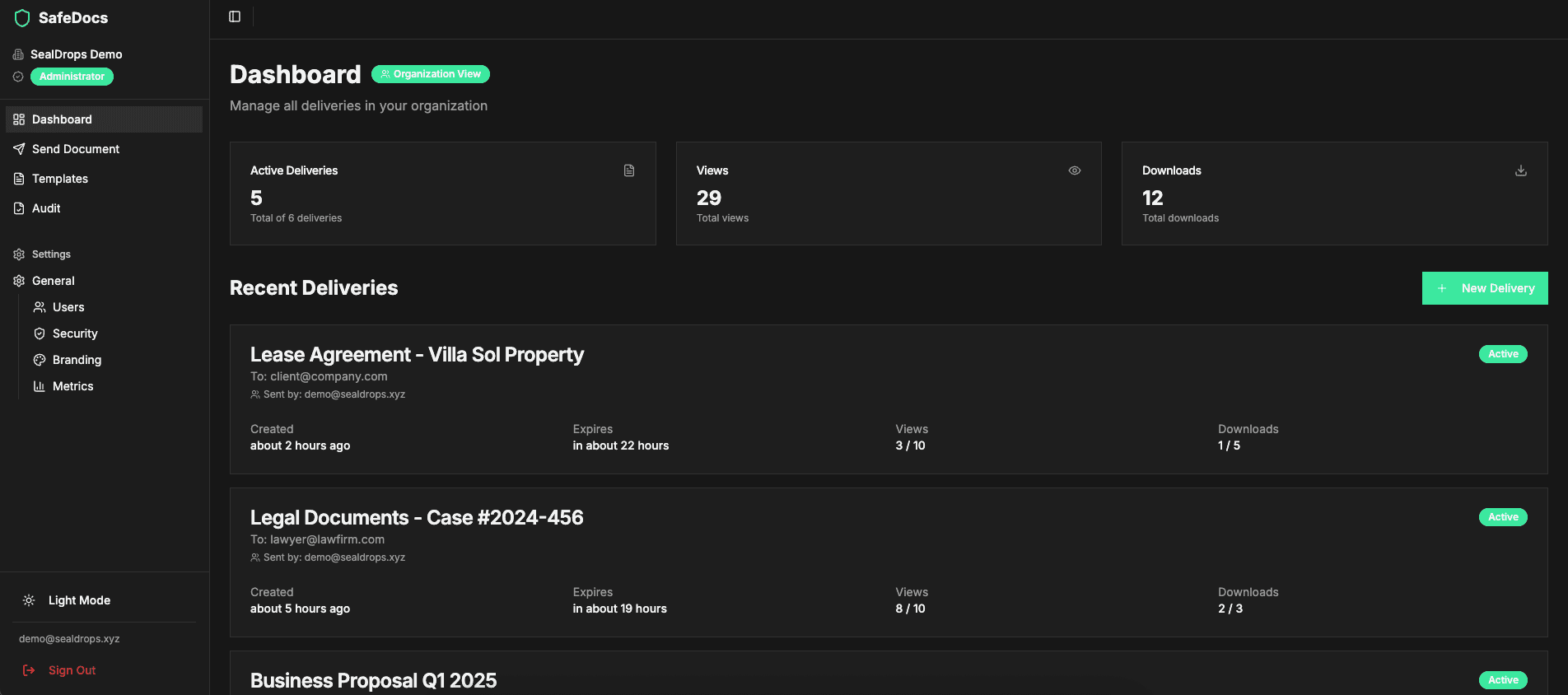
Track all your shared documents in one place
Share Documents
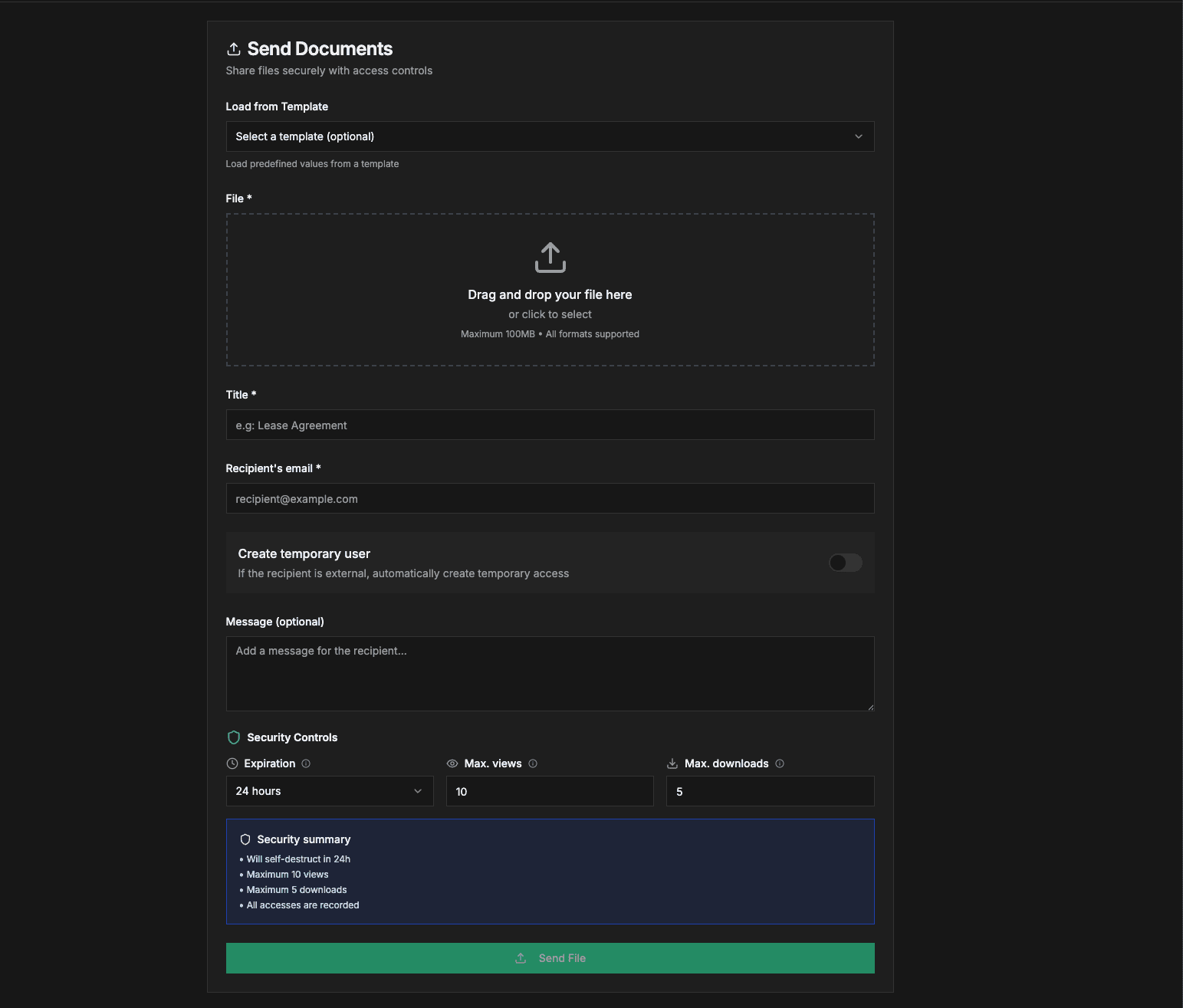
Simple upload with powerful controls
Complete Audit Trail
⭐ Our Differentiator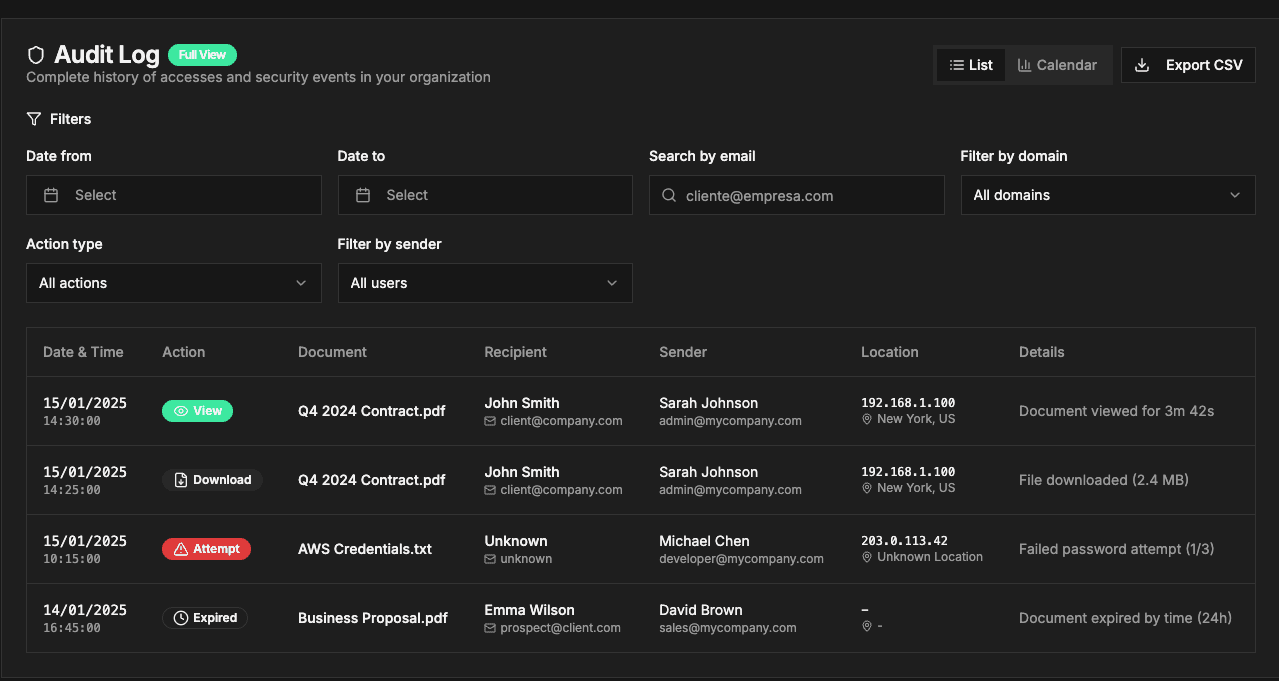
Every access logged with full details
Access Control
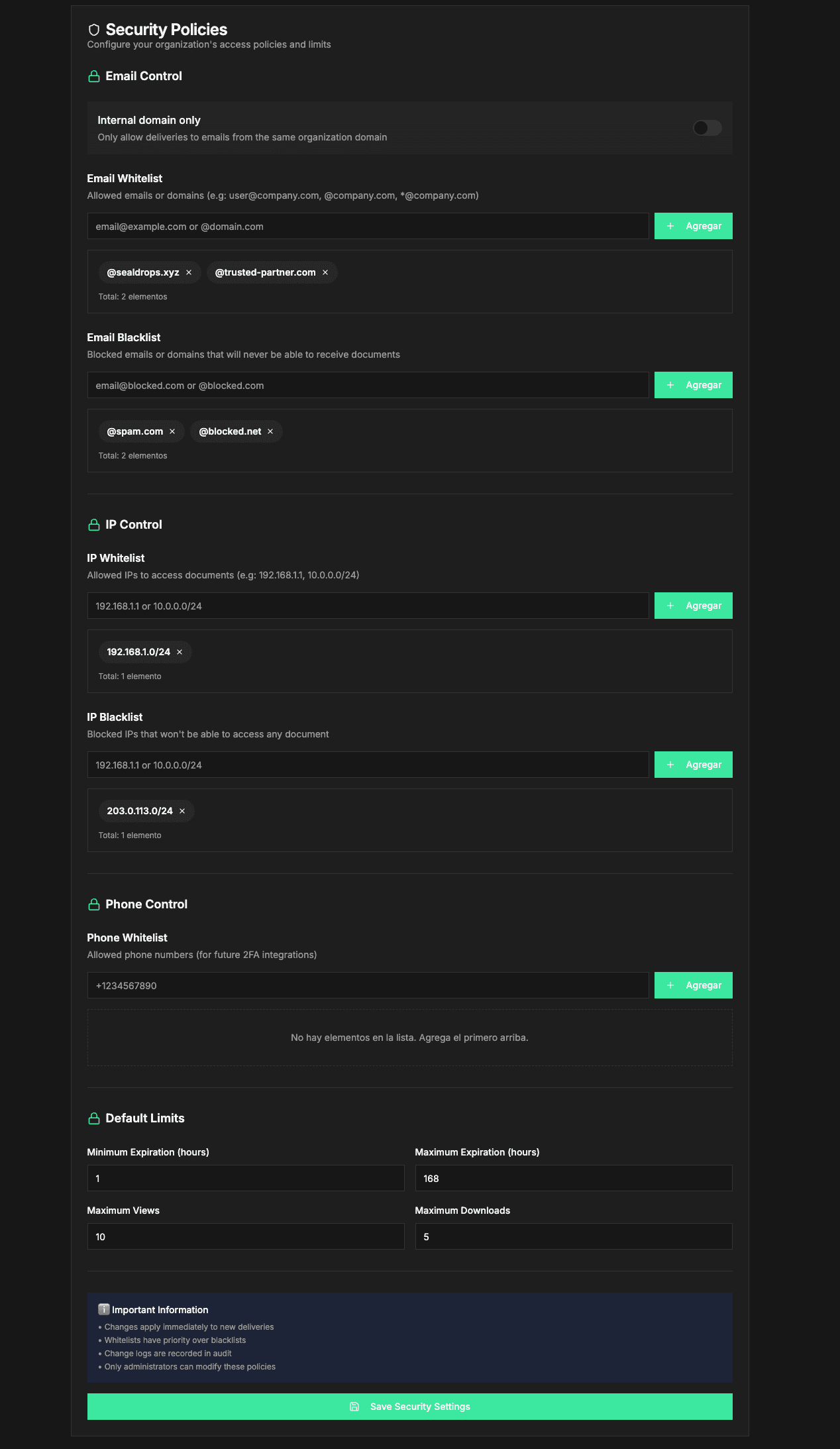
Configure expiration and security settings
Click any image to view full size
Ready to take control of your sensitive documents?
Security Features That Don't Exist Anywhere Else
Zero-trust access control meets forensic-grade audit trails
Zero-Trust Temporary Access
Recipients get single-use credentials with 4-digit tokens. No password recovery. No second chances.
- Auto-destructs after 2-3 failed login attempts
- Temporary user + token destroyed on failure
- Failed attempts logged in audit trail
Forensic-Grade Audit Trail
Track everything. Export everything. Prove everything.
- Who (email), when (timestamp), where (IP)
- Successful + failed access attempts
- CSV export for GDPR/HIPAA/SOC2 compliance
Mandatory IP Logging
No bypass. Senders must grant geolocation permission or cannot send.
- Works even with VPN (logs visible IP)
- Compliance-first design for regulated industries
- Track access patterns and anomalies
Multi-Trigger Self-Destruction
Documents destroy themselves when ANY condition is met.
- Time-based (1 hour to 30 days)
- View/download limits reached
- Failed authentication attempts (unique)
Verified Sender Identity
Google OAuth for senders. Anonymous zero-knowledge tokens for recipients.
- Senders authenticated via Google OAuth
- Bank-level AES-256 encryption
- Files never pass through email servers
Simple UX, Enterprise Power
Share files in seconds. Admin controls for teams.
- Up to 300MB per file
- Team management & policy configuration
- Full-text search across audit logs
Enterprise Compliance, Zero Effort
Sealdrop meets the strictest data protection standards worldwide
GDPR Compliant
European Union
- Data minimization through auto-deletion
- AES-256 encryption (Article 32)
- Storage limitation principle
- Accountability with audit trails
HIPAA Ready
Healthcare USA
- 6-year audit log retention (§164.312)
- Encrypted storage & transmission
- Access controls with audit trails
- Immutable logs for PHI access
CCPA/CPRA Aligned
California USA
- Auto-deletion within 45 days
- Data minimization by design
- Retention disclosure to users
- 24-month request records
Chile Ley 19.628
Chilean Data Protection
- Automatic data elimination (Art. 6)
- Professional secrecy (Art. 7)
- Immutable audit logging
- Cross-border transfer controls
Additional Standards
Ready to Secure Your Documents?
Be among the first to get complete audit trail and self-destructing links for your sensitive files.
Frequently Asked Questions
Everything you need to know about secure file sharing
